Both TCP/IP Model and OSI Reference Model have layered architecture and also their functionality almost look similar.
The main difference between them is, OSI reference model provides clear distinction between services,interface and protocols, whereas, TCP/IP doesn’t able to differentiate between them.
Difference between TCP/IP And OSI Reference Model in Tabular form
| Basis | TCP/IP Model | OSI Reference Model |
|---|---|---|
| Full form | Stands for Transmission Control Protocol/Internet Protocol | Open Systems Interconnection Reference Model |
| Definition | It defines standardised rules that enables network communication between computer as the internet | It facilitates open communication systems to communicate using Standard Protocols |
| Number of Layers | TCP/IP model has 4 layers, namely: Application layer Transport layer Internet layer Network access layer | OSI model has 7 layers, namely: Application layer Presentation layer m,Session layer, Transport layer, Network layer, Data link layer, Physical layer |
| Developed by | TCP/IP model was developed by DoD (Department of Defence) | OSI model was developed by ISO (International Standard Organisation) |
| Approach follow | Horizontal approach | Vertical approach |
| Transport layer | Both Connection-oriented and Connection-less | Connection-oriented |
| Differentiation | Doesn't differentiate between services,interface and protocols | Differentiates between services,interface and protocols |
| Upper Layer definition | Application Layer is corresponds to Application, Presentation and Session Layer of OSI Model | It is separately defined |
| Reliability | More | Less |
| Packet delivery by Transport Layer | Doesn't guarantee data packet delivery | Guarantees data packet delivery |
| Usage | Use in computer network | No longer in use |
| Routing protocols and standards definition | Internet Layer | Network Layer |
| Stability and Restrictions | Don't have strict boundaries and is more stable | Strict boundaries and is less stable |
TCP/IP Model
TCP/IP model is older than OSI model and consists 4 layer initially ,later on one more layer were added.
It defines standardised rules that enables network communication between computer as the internet.
These are the layers :-
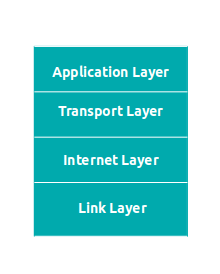
- Application Layer
It corresponds to Application, Presentation and Session Layer of OSI Model. It contains all the high-level protocols. It provides various services to perform user activities ranging from file transfer to internet surfing.
It consists of HTTP, SMTP, FTP protocols and more.
- Transport Layer
It ensures reliable transmission of data that is sent between hosts in the form of datagrams. It supports flow control and error control to make sure data is received at destination host reliably and correctly.
TCP(Transmission Control Protocol) and UDP(User Datagram Protocol) are protocols used in this layer.
- Internet Layer
It is responsible for transmitting data packets between hosts on a network. It routes independent data packets to correct host. It uses IP(Internet Protocol), ICMP (Internet Control Message Protocol) and ARP ( Address Resolution) protocol to achieve its function.
- Link Layer
It is a combination of the Data Link layer and Physical layer of OSI Model. It acts as an interface between transmission links and hosts. It uses a physical address to find hosts and send data.
OSI Reference Model
OSI Model stands for Open System Interconnection reference model which was developed by ISO. It facilitates open communication systems to communicate using Standard Protocols.
It is not a network architecture as it only states what a layer should do, but not describes the exact services and protocol to be used in each layer.
It follows certain principles on the basis of which it came to the decision of having 7 layers. Each and every layer has its own separate functionality.
These are the following 7 layers in OSI model :-
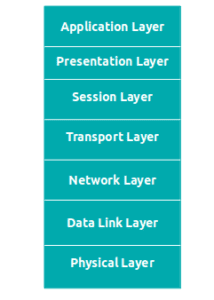
- Application Layer
It is the only layer that communicates with users for data directly. Network applications such as Skype, Chrome and other applications work in this layer.
They use application layer protocols such as HTTP, SMTP, FTP, POP3 to function. Application layer provides various services to perform user activities ranging from file transfer to internet surfing.
Presentation Layer
It accepts data from the application layer in the form of a sequence of numbers or characters and transforms it into a machine-understandable form which is binary data (10101010).
After that, data compression is used to reduce the size of the data before handing it over to the next layer. It accelerates the data transmission speed and therefore, it helps in case of video calls.
Lastly, data encryption is used to encrypt data in order to maximise the integrity and security. It secures the transmitting data from intruders.
SSL protocol is one of the protocols used in this layer
Objective Highlights
- Data Translation
- Data Compression
- Data Encryption
Session layers
It establishes, maintains, manages, and terminates connection or sessions between hosts. It uses various APIs (Application Programming Interface) to connect computers.
When a client requests for connection setup, the server uses authentication and authorisation before allowing the client to use its resources. Authentication can be defined as a process of identifying a user.
The authorisation is a process of identifying the access rights of a user, deciding what resources are allowed to access. Session layer also keeps track of which data packets belong to which file.
Objective Highlights
- Session Establishment
- Session Management
- Session Termination
Transport Layer
It ensures communication reliability by performing segmentation, error control and flow control.
It accepts data from the session layer and divides it into various segments and each segment consists of the information of the source, destination port number and sequence number. This is known as segmentation.
Port number is used to deliver the data to correct application, whereas the sequence number is used to put the data into the correct sequence.
Further, flow control handles the amount or size of data to be transmitted. Error control comes handy when a data packets are dropped in between transmission & not reached to the destination, then using various techniques, it retransmits data again. It also uses a checksum to identify the received corrupted segment.
Objective Highlights
- Data Segmentation
- Error Control
- Flow Control
Network Layer
This layer is responsible for transmitting received data segments from source host to destination host over a network.
It performs functions like logical addressing, routing and path determination. In this, each data unit is referred as data packets.
IP addressing done in this layer is called logical addressing. Each computer has an IP address to get uniquely identified on a network.
It assigns sender’s and receiver’s address to each segment, so, that they can reach at correct destination. Furthermore,
routing is also used to find an efficient and effective path from source to destination.
Lastly, path determination can be defined as a technique to select the best path for data delivery. OSPF, BGP, IS-IS are some protocols used in this layer.
Objective Highlights
- Logical Addressing
- Routing
- Path Determination
- Data Link Layer
It accepts data from the network layer. It performs physical addressing that is used to assign MAC address of sender and receiver host to received data packets to form a frame.
It also ensures the data transmission from one node to other must be error-free. It also takes care of the problem of controlling access to the shared channel using a sublayer called medium access control.
- Physical Layer
It converts data received from the data link layer to bitstream and is responsible for actual connectivity between the devices.
It involves physical equipment ranging from cables to switches for data transfer.